Configuring WebLogic GridLink DataSource with secure SCAN URL and secure ONS
Configuring SCAN and ONS on WLS GridLink datasource is already covered in Oracle whitepaper here
In this discussion today, I will list high level steps that are needed to configure secure SCAN and secure ONS on WLS GridLink Datasource instead of using their plain counterparts.
Here are the high level steps:
1) TCPS based listener configuration needs to be implemented on DB server side. Once it is done, we would get a secure SCAN URL. Based on this scan URL, we would get jdbc URL for use with our GridLink datasource, something like:
jdbc:oracle:thin:@(DESCRIPTION=(ADDRESS_LIST=(ADDRESS=(PROTOCOL=TCPS)(HOST=sup.oracle.vm)(PORT=1523)))(CONNECT_DATA=(SERVICE_NAME=racdb.oracle.vm)))
2) ONS daemons running on RAC nodes need to be secured as well with user certificate (using wallet). Note that it is essential to have ditto wallet configuration in following(or equivalent) files to secure ONS daemon successfully:
node1:
ons.config
ons.config.node1
node2:
ons.config
ons.config.node2
Here is sample output of ons.config and ons.config.node1 from node1
[grid@sup1 conf]$ cat ons.config
localport=6100 # line added by Agent
allowgroup=true
usesharedinstall=true
remoteport=6200 # line added by Agent
nodes=node1:6200,node2:6200 # line added by Agent
debugcomp=ons[all]
walletfile=/u01/app/11.2.0/grid2/network/admin/cost
walletpassword=welcome1
[grid@sup1 conf]$ cat ons.config.node1
localport=6100 # line added by Agent
allowgroup=true
usesharedinstall=true
remoteport=6200 # line added by Agent
nodes=node1:6200,node2:6200 # line added by Agent
debugcomp=ons[all]
walletfile=/u01/app/11.2.0/grid2/network/admin/cost
walletpassword=welcome1
3) With above things in place, just follow the steps in doc:
http://www.oracle.com/technetwork/middleware/weblogic/wls-jdbc-gridlink-howto-333331.html
Now some security specific highlights are:
4) Following needs to added to DOMAIN_HOME/setDomainEnv.sh:
set WEBLOGIC_CLASSPATH=D:\oracle\wls1034\modules\com.oracle.osdt_cert_1.0.0.0.jar;D:\oracle\wls1034\modules\com.oracle.osdt_core_1.0.0.0.jar;D:\oracle\wls1034\modules\com.oracle.oraclepki_1.0.0.0.jar;%WEBLOGIC_CLASSPATH%
What this does is it pulls these jar files into classpath so that WebLogic can play with Oracle wallets.
5) GridLink datasource security related configuration is:
keystore Driver Properties:
---------------------------------------
javax.net.ssl.keyStore=D:\\apps\\rac_db_repro\\identity_against_db.jks
javax.net.ssl.keyStorePassword=welcome1
javax.net.ssl.keyStoreType=JKS
javax.net.ssl.trustStore=D:\\apps\\rac_db_repro\\db_trust.jks
javax.net.ssl.trustStorePassword=welcome1
javax.net.ssl.trustStoreType=JKS
Note:
a) "identity_against_db.jks" is nothing but Java Keystore that has user certificate (used as client identity)
b) "db_trust.jks" contains root certificate(s) of CA(s) who signed user certificate(s) used by DB process
6) ONS nodes in GridLink datasource used:
node1.oracle.vm:6200
node2.oracle.vm:6200
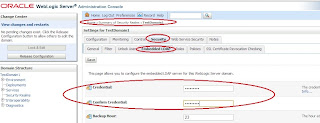
7) wallet in ONS configuration on GridLink datasource used:
ons-wallet-file --> D:\apps\rac_db_repro
ons-wallet-password --> welcome1
Note
a) the wallet file is "ewallet.p12", and is located at "D:\apps\rac_db_repro"
b) "ewallet.p12" contains root certificate(s) of CA(s) who signed user certificate(s) used by ONS process
In this discussion today, I will list high level steps that are needed to configure secure SCAN and secure ONS on WLS GridLink Datasource instead of using their plain counterparts.
Here are the high level steps:
1) TCPS based listener configuration needs to be implemented on DB server side. Once it is done, we would get a secure SCAN URL. Based on this scan URL, we would get jdbc URL for use with our GridLink datasource, something like:
jdbc:oracle:thin:@(DESCRIPTION=(ADDRESS_LIST=(ADDRESS=(PROTOCOL=TCPS)(HOST=sup.oracle.vm)(PORT=1523)))(CONNECT_DATA=(SERVICE_NAME=racdb.oracle.vm)))
2) ONS daemons running on RAC nodes need to be secured as well with user certificate (using wallet). Note that it is essential to have ditto wallet configuration in following(or equivalent) files to secure ONS daemon successfully:
node1:
ons.config
ons.config.node1
node2:
ons.config
ons.config.node2
Here is sample output of ons.config and ons.config.node1 from node1
[grid@sup1 conf]$ cat ons.config
localport=6100 # line added by Agent
allowgroup=true
usesharedinstall=true
remoteport=6200 # line added by Agent
nodes=node1:6200,node2:6200 # line added by Agent
debugcomp=ons[all]
walletfile=/u01/app/11.2.0/grid2/network/admin/cost
walletpassword=welcome1
[grid@sup1 conf]$ cat ons.config.node1
localport=6100 # line added by Agent
allowgroup=true
usesharedinstall=true
remoteport=6200 # line added by Agent
nodes=node1:6200,node2:6200 # line added by Agent
debugcomp=ons[all]
walletfile=/u01/app/11.2.0/grid2/network/admin/cost
walletpassword=welcome1
3) With above things in place, just follow the steps in doc:
http://www.oracle.com/technetwork/middleware/weblogic/wls-jdbc-gridlink-howto-333331.html
Now some security specific highlights are:
4) Following needs to added to DOMAIN_HOME/setDomainEnv.sh:
set WEBLOGIC_CLASSPATH=D:\oracle\wls1034\modules\com.oracle.osdt_cert_1.0.0.0.jar;D:\oracle\wls1034\modules\com.oracle.osdt_core_1.0.0.0.jar;D:\oracle\wls1034\modules\com.oracle.oraclepki_1.0.0.0.jar;%WEBLOGIC_CLASSPATH%
What this does is it pulls these jar files into classpath so that WebLogic can play with Oracle wallets.
5) GridLink datasource security related configuration is:
keystore Driver Properties:
---------------------------------------
javax.net.ssl.keyStore=D:\\apps\\rac_db_repro\\identity_against_db.jks
javax.net.ssl.keyStorePassword=welcome1
javax.net.ssl.keyStoreType=JKS
javax.net.ssl.trustStore=D:\\apps\\rac_db_repro\\db_trust.jks
javax.net.ssl.trustStorePassword=welcome1
javax.net.ssl.trustStoreType=JKS
Note:
a) "identity_against_db.jks" is nothing but Java Keystore that has user certificate (used as client identity)
b) "db_trust.jks" contains root certificate(s) of CA(s) who signed user certificate(s) used by DB process
6) ONS nodes in GridLink datasource used:
node1.oracle.vm:6200
node2.oracle.vm:6200
7) wallet in ONS configuration on GridLink datasource used:
ons-wallet-file --> D:\apps\rac_db_repro
ons-wallet-password --> welcome1
Note
a) the wallet file is "ewallet.p12", and is located at "D:\apps\rac_db_repro"
b) "ewallet.p12" contains root certificate(s) of CA(s) who signed user certificate(s) used by ONS process
Comments
Post a Comment