Disabling the non-ssl port of management server (EMGC_OMSx) when using self-signed certificates ( and OHS is already secured) (in Oracle Grid Control 11g)
Goal:
Goal of this document is to help disabling the non-ssl port of EMGC_OMS1 in 11g Grid Control environment such that communication to this server is limited to secure port only come what may.
Sounds easy!!! Nope, it is not. Agents (for uploading the data) and browsers (for accessing EM console) used to connect to this server via front-end OHS server. This OHS server used to talk to our EMGC_OMS1 server over non-secure port (confirm this for you in mod_wl_weblogic.conf ). By disabling non-secure port, we have effectively disabled this access.
This document assumes
- that WebLogic is already running using self-signed certificates.
- OHS layer is secured (using 3rd part/self-signed/default certificates)
If OHS is secured with default certificates, and you want to secure OHS with self signed and disable OMS non-secure port side-by-side, please wait for my next post.
How:
These are the colors your brain will intercept while reading this article:
- This background color is for commands
- This background color is for entries in some file
- This background color is for something that exists (or is going to exist) on filesystem
Before setting out, please ensure that we have a copy of public certificate (in PEM format) corresponding to WebLogic’s self-signed keypair. If you don’t have it, extract it using “keytool” command like this:
keytool -exportcert -alias <self-signed_cert_alias> -keystore <keystore_name> -storetype jks -storepass <keystore_password> -keypass <private_key_password> -file < filename>
e.g., keytool -exportcert -alias wlsmac2 -keystore identity.jks -storetype jks -storepass mypass -keypass mypass -file wlsmac2.cer
e.g., keytool -exportcert -alias wlsmac2 -keystore identity.jks -storetype jks -storepass mypass -keypass mypass -file wlsmac2.cer
java utils.der2pem <input_der_file>
This will generate PEM certificate into the same directory with same file name but with "pem" extension. Note that this utility will expect the input file to be with "der" extension. So, rename "wlsmac2.cer" to "wlsmac2.der" before executing this command.
e.g., java utils.der2pem wlsmac2.der
Note: If you get any "java.lang.ClassNotFoundException" command while trying to execute this utility, try setting the weblogic environment using script gc_inst/user_projects/domains/GCDomain/bin/setDomainEnv.sh. E.g.,
. ./setDomainEnv.sh #after cd to "gc_inst/user_projects/domains/GCDomain/bin/"
The actual steps are:
1) Ensure Grid Control is up using command:
emctl status oms
2) Bring up WebLogic administration console using browser:
https://host:secure_port/console
https://host:secure_port/console
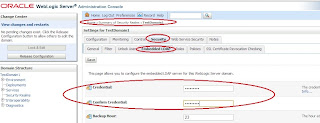
3) Navigate to tab Servers/EMGC_OMS1/Configuration/General
4) Click on “Lock and Edit” button in change center
5) Uncheck the checkbox next to “Listen Port Enabled”
6) Click on button “Save”
7) Click on “Activate Change”
8) Edit "emgc.properties" file and set already defined parameter "MSPORT" to 0:
MSPORT=0
9) Shutdown grid control using command:
emctl stop oms
10) As OHS has to talk to ssl port of EMGC_OMS1 server and this will involve certificate exchange (OHS has to trust the incoming certificate of EMGC_OMS1 server). This trust is loaded from wallet located at:
$(ORACLE_INSTANCE)/config/OHS/ohs1/keystores /proxy
So we need to create a new wallet with weblogic certificate (as trusted entry) in it. We can replace the default wallet with our new wallet however there is one trouble here- this wallet gets reset each time we execute following command(i.e., without “-wallet” switch):
emctl secure oms
Hence, what we will do is we will setup this wallet in custom location, say at:
$(ORACLE_INSTANCE)/config/OHS/ohs1/keystores /my_proxy
If you are not interested in this (means you will have to take care not to execute “emctl secure oms “ accidentally), please drop to step-11.
To implement this,
a) Navigate to directory:
${ORACLE_HOME} /oms11g/sysman/config
- Take a backup of file “mod_wl_ohs.conf.template” and edit the original one.
- Locate following line:
&SECURE_PROXY& WlSSLWallet ${ORACLE_INSTANCE/config/${COMPONENT_TYPE}/${COMPONENT_NAME}/keystores/proxy
- Replace it like this:
&SECURE_PROXY& WlSSLWallet ${ORACLE_INSTANCE/config/${COMPONENT_TYPE}/${COMPONENT_NAME}/keystores/my_proxy
- Save it
b) Create directory
$(ORACLE_INSTANCE)/config/OHS/ohs1/keystores /my_proxy
$(ORACLE_INSTANCE)/config/OHS/ohs1/keystores /my_proxy
11) Making OHS server aware that WebLogic is no longer available on non-ssl port:
a) Navigate to directory
$(ORACLE_INSTANCE)/config/OHS/ohs1 and edit file “mod_wl_ohs.conf”
$(ORACLE_INSTANCE)/config/OHS/ohs1 and edit file “mod_wl_ohs.conf”
b) set “WebLogicPort” equal to EMGC_OMS1 server’s ssl port. Like:
WebLogicPort 7301
Note:- If you do not know what the ssl port is, look for:
-> Property “MS_HTTPS_PORT” in emgc.properties file
-> Field “SSL Listen Port:” in Weblogic Administration (console under tab servers/EMGC_OMS1/Configuration/General)
c) Locate and uncomment following line:
#SecureProxy On
d) Locate following commented line
#WlSSLWallet ${ORACLE_INSTANCE}/config/${COMPONENT_TYPE}/${COMPONENT_NAME}/keystores/proxy
Replace it with following modified uncommented line:
WlSSLWallet ${ORACLE_INSTANCE}/config/${COMPONENT_TYPE}/${COMPONENT_NAME}/keystores/my_proxy
Or (if you opted not to follow step-10):
WlSSLWallet ${ORACLE_INSTANCE}/config/${COMPONENT_TYPE}/${COMPONENT_NAME}/keystores/proxy
12) Creating our new wallet (at “ohs1/keystores/my_proxy” or at “ohs1/keystores/proxy”, depending upon how you preferred step-11):
a) Navigate to “ohs1/keystores/my_proxy” or (“ohs1/keystores/proxy”). Create a new blank wallet:
orapki wallet create -wallet ./
Remember the wallet password. You will need this in future if you want to modify the wallet.
b) Now import Weblogic/OMS certificate as a trust certificate into our new wallet:
orapki wallet add -wallet ./ -trusted_cert -cert ./wlsmac2.pem
At this point, confirm that we have all the trust cert in our new wallet using command:
orapki wallet display -wallet ./
c) Set wallet to auto-login (this will generate cwallet.sso file in same directory):
orapki wallet create -wallet ./ -auto_login
d) Make sure that the OS user whom you use to start the OMS server (executing “emctl start oms”) has read/execute permission on cwallet.sso and ewallet.p12 files in this directory.
13) start the grid control using command, and we are done:
emctl start oms
Comments
Post a Comment