Securing OHS layer and disabling the non-ssl port of management server (EMGC_OMSx) when using self-signed certificates (in Oracle Grid Control 11g)
Make sure that we have:
Now here the steps:
1) Navigate to "/tmp". Import WebLogic CA certificate into OHS identity wallet using "orapki" utility like this:
This utility can be typically located at "<MIDDLEWARE_HOME>/oracle_common/bin" in Grid Control setup.
2) Generate SSO wallet corresponding to OHS identity wallet using "orapki" utility:
This will generate file "cwallet.sso" in the same directory.
3) Ensure Grid Control is up, using command:
4) Bring up Weblogic administration console using browser:
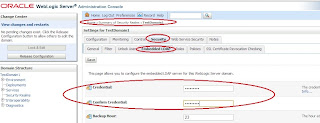
5) Navigate to tab Servers/EMGC_OMS1/Configuration/General
6) Click on 'Lock and Edit' button in change center
7) Uncheck the checkbox next to 'Listen Port Enabled'
8) Click on button 'Save'
9) Click on 'Activate Change'
10) Logout from console
11) Edit "emgc.properties" file and set already defined parameter "MSPORT" to 0:
This will tell "emctl start/stop oms" to connect to EMGC_OMS1 server over ssl port to bring it down, from now onwards.
12) Stop the OMS server:
13) Execute:
This command connects to EMGC_ADMIN and reads the port values from there. Since we have disabled non-ssl port of EMGC_OMS1 server, this command will automatically modify mod_wl_ohs.conf file and set following for you:
14) Copy the files "ewallet.p12", "cwallet.sso" and "CA_of_ohs.cer" (from "/tmp") into following location:
15) Execute:
This will copy the wallets from "proxy" directory into "upload" directory, overwriting any existing wallet.
16) Secure console with new certificate:
17) Force shutdown whole grid control:
18) Start the grid control:
19) Next we import the OHS' CA certificate into agent trust on all machines so that agent(s) can accepts/trust new OHS certificate, and upload is successful.
20) Stop and restart the agents for changes to take effect.
- Server certificate (which will correspond to identity of our OHS server). This certificate should be contained in "new" custom oracle wallet file named as "ewallet.p12". This certificate can be self-signed/3rd party signed (details of creating such a wallet are out of scope of this document). I will call this wallet as "OHS identity wallet" and the server certificate within it as OHS identity certificate from this point onwards.
- Root certificate of CA(Certifying authority) who signed OHS identity certificate. Say this is in file "CA_of_ohs.cer".
- Root certificate of CA who signed weblogic certificate. If you have used 3rd party signed certificate on weblogic, then this will be ROOT certificate of the corresponding CA. If you have used self-signed certificates on weblogic, then our "CA certificate" will be public certificate corresponding to self-signed keypair. We can get this by exporting it from the weblogic identity keystore using "keytool" like this:
keytool -exportcert -alias <self-signed_cert_alias> -keystore <keystore_name> -storetype jks -storepass <keystore_password> -keypass <private_key_password> -file < filename>
e.g.,
keytool -exportcert -alias wlsmac2 -keystore identity.jks -storetype jks -storepass mypass -keypass mypass -file wlsmac2.cer
Copy above files (ewallet.p12, CA_of_ohs.cer and wlsmac2.pem) into some temporary directory (let us say into "/tmp").
Note: Keytool exports the certificate into DER format. Consider getting PEM format of same certificate using java utility "utils.der2pem". Command is:
java utils.der2pem <input_der_file>
This will generate PEM certificate into the same directory with same file name but with "pem" extension. Note that this utility will expect the input file to be with "der" extension. So, rename "wlsmac2.cer" to "wlsmac2.der" before executing this command.
e.g., java utils.der2pem wlsmac2.der
Note: If you get any "java.lang.ClassNotFoundException" command while trying to execute this utility, try setting the weblogic environment using script gc_inst/user_projects/domains/GCDomain/bin/setDomainEnv.sh. E.g.,
. ./setDomainEnv.sh #after cd to "gc_inst/user_projects/domains/GCDomain/bin/"
I will call this certificate as "WebLogic CA certificate", and suppose it is there in file "wlsmac2.pem".
Now here the steps:
1) Navigate to "/tmp". Import WebLogic CA certificate into OHS identity wallet using "orapki" utility like this:
orapki wallet add -wallet ./ewallet.p12 -trusted_cert -cert ./wlsmac2.pem
This utility can be typically located at "<MIDDLEWARE_HOME>/oracle_common/bin" in Grid Control setup.
2) Generate SSO wallet corresponding to OHS identity wallet using "orapki" utility:
orapki wallet create -wallet ./ -auto_login
This will generate file "cwallet.sso" in the same directory.
3) Ensure Grid Control is up, using command:
OMS_HOME/bin/emctl status oms
4) Bring up Weblogic administration console using browser:
https://host:secure_port/console
5) Navigate to tab Servers/EMGC_OMS1/Configuration/General
6) Click on 'Lock and Edit' button in change center
7) Uncheck the checkbox next to 'Listen Port Enabled'
8) Click on button 'Save'
9) Click on 'Activate Change'
10) Logout from console
11) Edit "emgc.properties" file and set already defined parameter "MSPORT" to 0:
MSPORT=0
This will tell "emctl start/stop oms" to connect to EMGC_OMS1 server over ssl port to bring it down, from now onwards.
12) Stop the OMS server:
OMS_HOME/bin/emctl stop oms
13) Execute:
OMS_HOME/bin/emctl secure oms
This command connects to EMGC_ADMIN and reads the port values from there. Since we have disabled non-ssl port of EMGC_OMS1 server, this command will automatically modify mod_wl_ohs.conf file and set following for you:
WebLogicPort <secure_port_of_EMGC_OMS1>SecureProxy On #This tells OHS to connect to above port using secure protocolWlSSLWallet ${ORACLE_INSTANCE}/config/${COMPONENT_TYPE}/${COMPONENT_NAME}/keystores/proxy #This is where OHS will expect a wallet containing root certificate of CA who signed weblogic certificate
14) Copy the files "ewallet.p12", "cwallet.sso" and "CA_of_ohs.cer" (from "/tmp") into following location:
${ORACLE_INSTANCE}/config/${COMPONENT_TYPE}/${COMPONENT_NAME}/keystores/proxy
15) Execute:
OMS_HOME/bin/emctl secure oms -wallet <${ORACLE_INSTANCE}/config/${COMPONENT_TYPE}/${COMPONENT_NAME}/keystores/proxy> -trust_certs_loc <${ORACLE_INSTANCE}/config/${COMPONENT_TYPE}/${COMPONENT_NAME}/keystores/proxy/CA_of_ohs.cer>
This will copy the wallets from "proxy" directory into "upload" directory, overwriting any existing wallet.
16) Secure console with new certificate:
OMS_HOME/bin/emctl secure console -wallet <${ORACLE_INSTANCE}/config/${COMPONENT_TYPE}/${COMPONENT_NAME}/keystores/proxy>
17) Force shutdown whole grid control:
OMS_HOME/bin/emctl stop oms -force -all
18) Start the grid control:
OMS_HOME/bin/emctl start oms
19) Next we import the OHS' CA certificate into agent trust on all machines so that agent(s) can accepts/trust new OHS certificate, and upload is successful.
AGENT_HOME/bin/emctl secure add_trust_cert -trust_certs_loc CA_of_ohs.cer ----> (file is from requirement-b as discussed at the start of this topic)
20) Stop and restart the agents for changes to take effect.
Comments
Post a Comment